Controlled folder access is a nice new feature to Windows 10 1709 Fall Creators Update. Although CFA claims to enable certain defaults for Windows programs, I’ve found that all but “Camera” in Windows 10 keeps getting popped.
There wasn’t much I could find on how to add Group Policy exceptions for CFA so I experimented until I got it right for my domain. I tested this in our dev JLTCsecurityGroup.com domain with no issues. I then deployed to a small enterprise and voila. Success nearly out the box.
- Get the 1709 ADMX files from here: https://www.microsoft.com/en-us/download/details.aspx?id=56121
- Install and extract. For me I extracted to my Server 2016 Central Store. Doing this remotely on a core server from a jumpbox looked like this: \\[server name]\c$\Windows\SYSVOL\domain\Policies\PolicyDefinitions\
- Open the GPO of choice on the Group Policy Management snap-in
- Navigate to Computer Config: Windows components > Windows Defender Antivirus > Windows Defender Exploit Guard > Controlled folder access. *Note there are two “Windows Defender Exploit Guard” locations. You’ll want the green box for this exercise.
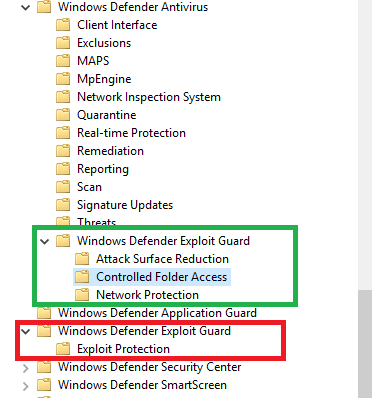
- Navigate over to “Controlled Folder Access” and enable “Configure Controlled folder access” to your liking.
- Jump over to “Configure allowed applications” and note these Windows apps that I enabled access for because, from the default controls, I couldn’t save to protected locations using Word, Notepad, Snipping Tool, and others. I haven’t played “Value name” and “Value” I simply duplicated in both fields. This is what it looks like in production.
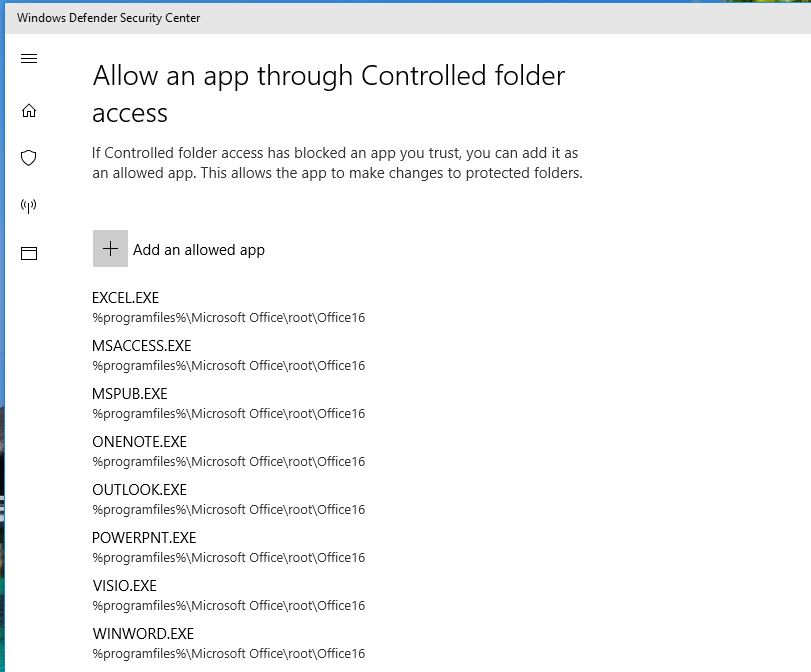 This is the view from the GPO side:
This is the view from the GPO side:
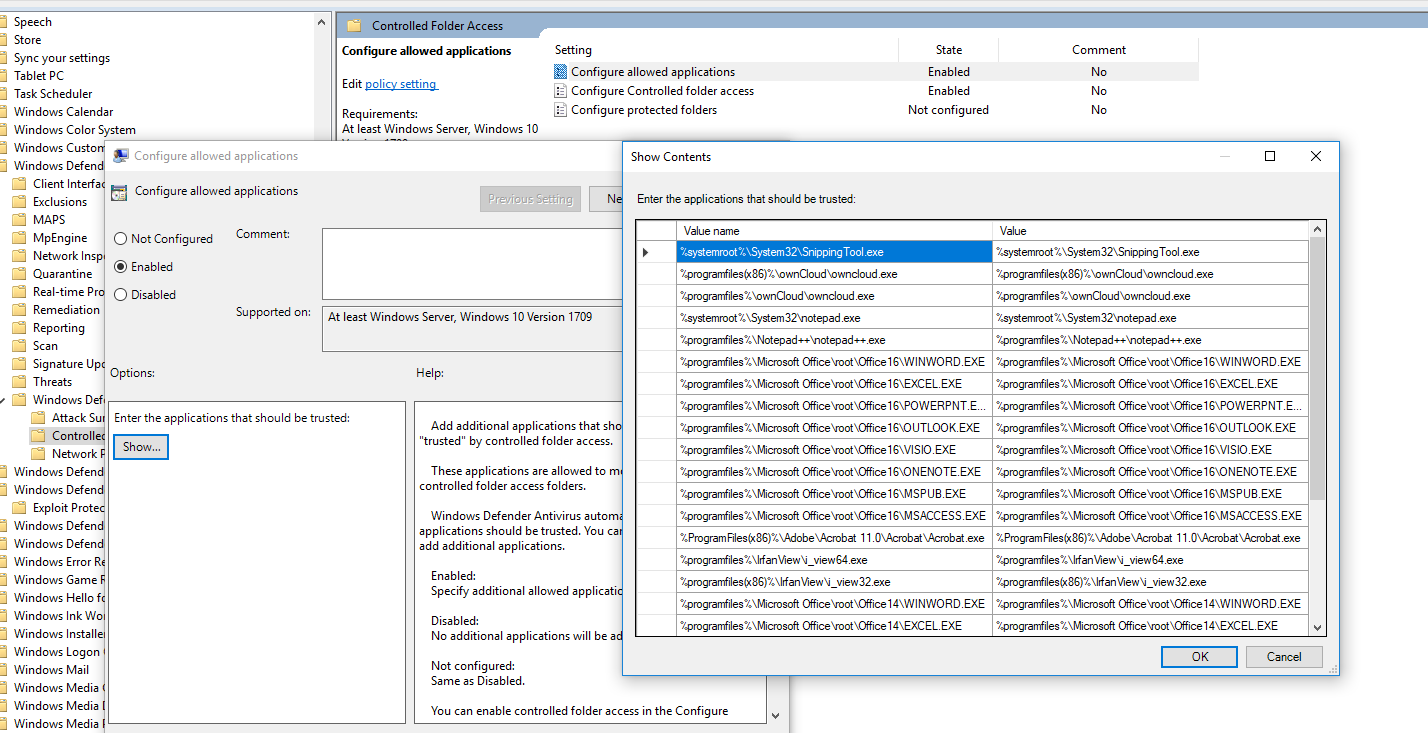 And finally a raw list of Microsoft apps (I dropped some of my custom ones like IrfanView, Notepad++, and Adobe):
And finally a raw list of Microsoft apps (I dropped some of my custom ones like IrfanView, Notepad++, and Adobe):
%systemroot%\System32\SnippingTool.exe
%systemroot%\System32\notepad.exe
%programfiles%\Microsoft Office\root\Office16\WINWORD.EXE
%programfiles%\Microsoft Office\root\Office16\EXCEL.EXE
%programfiles%\Microsoft Office\root\Office16\POWERPNT.EXE
%programfiles%\Microsoft Office\root\Office16\OUTLOOK.EXE
%programfiles%\Microsoft Office\root\Office16\VISIO.EXE
%programfiles%\Microsoft Office\root\Office16\ONENOTE.EXE
%programfiles%\Microsoft Office\root\Office16\MSPUB.EXE
%programfiles%\Microsoft Office\root\Office16\MSACCESS.EXE
%programfiles%\Microsoft Office\root\Office14\WINWORD.EXE
%programfiles%\Microsoft Office\root\Office14\EXCEL.EXE
%programfiles%\Microsoft Office\root\Office14\POWERPNT.EXE
%programfiles%\Microsoft Office\root\Office14\OUTLOOK.EXE
%programfiles%\Microsoft Office\root\Office14\VISIO.EXE
%programfiles%\Microsoft Office\root\Office14\ONENOTE.EXE
%programfiles%\Microsoft Office\root\Office14\MSPUB.EXE
%programfiles%\Microsoft Office\root\Office14\MSACCESS.EXE
%windir%\system32\mstsc.exe
There are some PowerShell options for CFA as well. I’ve pinged my buddy over at https://www.powershellmagic.com to see if he has anything scripted up for Controlled Folder Access. REF: https://docs.microsoft.com/en-us/windows/threat-protection/windows-defender-exploit-guard/enable-controlled-folders-exploit-guard
#MakeSecurityGreatAgain