The *nix community usually does a great job making it easy for tech savvy noobs to accomplish simple tasks but sometimes something that seems like it should be simple is complicated by the fact that the *nix folks compiling various *nix components are uber-geeks and they might forget “their roots”.
As an FYI, some settings (not the ones below) can be found in the clamav conf file at /etc/clamav/freshclam.conf
With that said, here is how I configured ClamAV to auto-scan various directories at 0300 every day and auto-remove any infections (thanks to four separate blog entries that I’ve pieced together). For all of this, I up-elevated with “sudo -i” and, unless otherwise noted, command entered into terminal prompt are followed with pressing “enter” on the keyboard:
apt-get install clamav clamav-daemon
freshclam
/etc/init.d/clamav-daemon start
nano /var/clamav-scan.sh
This should have installed clamav, updated clamav, and started clamav.
Within “clamav-scan.sh”, you will list the directories you want to scan. For me, I am scanning “/home/”, “/etc/”, “/opt/”, and (for me most importantly) “/var/www/”. The “–remove” command will auto-remove and files clamav determines to be infected, with prejudice. If you are CPU constrained, like a small Azure VM, drop the multiscan line or you will eat up CPU very quickly.
clamdscan /home/ /etc/ /opt/ /var/www/ --fdpass --infected --multiscan --remove
Write out the file (ctrl+o = save changes) and make the script executable:
chmod +x /var/clamav-scan.sh
Now we will schedule scans at 0300 daily using crontab:
crontab -e
00 03 * * * /var/clamav-scan.sh
Write out crontab (ctrl+o = save changes).
Now, let’s test ClamAV. CD to a directory that you want ClamAV to scan. For me, I will cd to /var/www. Once in /var/www, let’s use WGET to download an EICAR test anti-virus file. Note: If you have network-level AV scanning, you will need to bypass the EICAR test file on your network appliances. I wasn’t able to WGET the EICAR file and ran in circles until I realized my UTM appliance was knocking down the connection (and rightfully so).
wget https://www.eicar.org/download/eicar.com.txt
This should put “eicar.com.txt” in /var/www folder. Let’s manually launch ClamAV and make sure it nukes the EICAR test file. From a terminal prompt, simply execute the script:
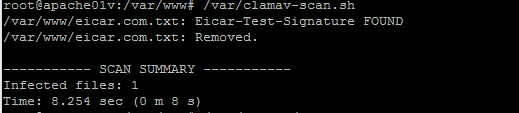
/var/clamav-scan.sh
You should see that (hopefully) one, and only one file was detected and nuked. If more than one file has been found then you’re welcome. :p