Configuring AT&T WIFI calling is a pretty straight forward and simple process but there is a caveat. AT&T WIFI uses IMAP and VPN ports which may be blocked to prevent outbound VPN or certain email sessions established from within the business or enterprise. If you are doing deep packet inspection, Untangle NG Firewall may also flag or categorize your AT&T WIFI VoIP traffic as IMAP (mail) traffic which could be marked as low-priority and impact your VoIP quality.
So, how can we properly allow AT&T WIFI calling out of our business or enterprise protected by Untangle NG Firewall 13.x while still maintaining proper outbound security controls around unauthorized VPN traffic? Easy! Mark the destination CIDR blocks with your TCP/UDP ports outbound as AT&T WIFI, bypass this combination in Bypass Rules (so this combination isn’t inspected), and give them priority in your QoS settings.
The AT&T LAN configuration page (https://www.att.com/esupport/article.html#!/wireless/KM1114459) states that the following ports need outbound access:
- UDP 500
- UDP 4500
- TCP 143
Additionally, access to the following FQDNs are required:
- epdg.epc.att.net
- sentitlement2.mobile.att.net
- vvm.mobile.att.net
The IP/CIDR* blocks for these FQDNs are as follows:
- 129.192.0.0/16 – https://whois.arin.net/rest/net/NET-129-192-0-0-1/pft?s=129.192.164.10
- 166.128.0.0/9 – https://whois.arin.net/rest/net/NET-166-128-0-0-1/pft?s=166.137.140.129
- (Same as 2 above): 166.128.0.0/9
*If you wanted to get granular, you can do an NSLOOKUP of the 3 FQDNs and only allow those IPs through but they may change. Depending on your level of risk you should either allow only those IPs or the entire CIDR block.
- Now for the technical part. Log in to your Untangle NG Firewall and go to “Config” at the top of the page then navigate to “Network“.
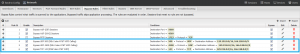
- Go to “Bypass Rules” and add three rules: one rule for UDP port 500 to destination addresses 129.192.0.0/16,166.128.0.0/9 or the IPs that the NSLOOKUP resolves, a second rule for UDP port 4500 to destination addresses 129.192.0.0/16,166.128.0.0/9 or the IPs that the NSLOOKUP resolves, and a third rule for TCP port 143 to destination addresses 129.192.0.0/16,166.128.0.0/9 or the IPs that the NSLOOKUP resolves.
 Cheap and easy route: download and append to current rules this JSON rule set: https://www.dropbox.com/s/rzzmlttju3iup81/ATT-WIFI-Untangle-13-Bypass-Rules.json?dl=0
Cheap and easy route: download and append to current rules this JSON rule set: https://www.dropbox.com/s/rzzmlttju3iup81/ATT-WIFI-Untangle-13-Bypass-Rules.json?dl=0 -
- MD5 HASH: 064e4573f651ce65b6c04796098853dc
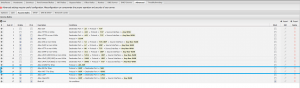
- Next, go to “Advanced” tab then “Access Rules“. Ensure that your IKE and NAT-T are enabled for IPv4 and/or IPv6 (depending on your needs).
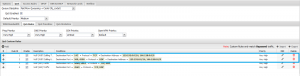
- Finally go to “QoS‘ tab then “QoS Rules” sub-tab and add your AT&T WIFI rules again. We’ll create two rules: one for destination protocol TCP, port 143, with destination addresses used in section 2 (either CIDR blocks 129.192.0.0/16,166.128.0.0/9 or the IPs from NSLOOKUP) and a second rule for destination protocol UDP, ports 500 and 4500, with destination addresses used in section 2 (either CIDR blocks 129.192.0.0/16,166.128.0.0/9 or the IPs from NSLOOKUP).
 Cheap and easy route: download and append to current rules this JSON rule set: https://www.dropbox.com/s/hgk2u0tlm3p9wo8/ATT-WIFI-Untangle-13-QoS-Rules.json?dl=0
Cheap and easy route: download and append to current rules this JSON rule set: https://www.dropbox.com/s/hgk2u0tlm3p9wo8/ATT-WIFI-Untangle-13-QoS-Rules.json?dl=0 -
- MD5 HASH: 4bb512d9eda1e968956645e4ddc6c69c
If you are using an Apple iPhone configured for WIFI calling, join the wireless network that is behind the Untangle NG Firewall that we just configured. Swipe “up” to disable cellular.
Once cellular is disabled your device will/should switch to AT&T WIFI. Test a call and ensure that the WIFI calling works and check for clarity. Don’t forget to re-enable your cellular!
 *NOTE: This architecture has not been security validated (peer reviewed) and has only been tested for functionality. If you validate the security aspects of this please let me know in the comments.
*NOTE: This architecture has not been security validated (peer reviewed) and has only been tested for functionality. If you validate the security aspects of this please let me know in the comments.
Trying these steps with Untangle NGFW 14 with Bypass Rules and QoS. Before this the WiFi calling latency was making me crazy. Will see how it performs after this configuration update.
Why do you use 129.192.0.0/0 in the rule instead of 129.192.0.0/16 which was listed in the WHOIS?
Uh… that’s a typo and pretty big one indeed. Not sure how Untangle even took it. I know how I made that mistake but won’t share that here 😉 . Thanks for catching it.
I updated the post, the pictures, the rules, and the rule hashes.