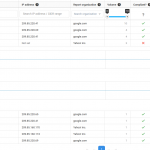
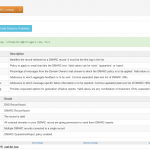
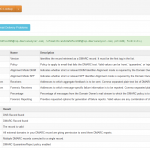
I’m doing some email forensic analysis this morning on my personal domains (johndball.com and laurenball.com) and it reminded me of a scenario.
A certain company spent a considerable sum on an advanced “AI driven” email security tool. While the tool is pretty darn neat, and it came with a pretty darn expensive price tag, they failed to implement the basics. When trying to figure out why they were seeing an uptick in phishing emails and BEC, and why this tool wasn’t catching it properly, I pointed out that they had no DMARC, SPF, or DKIM records.
Too many times a new tool, product, or solution shows up in the form of a cold call, email to the CIO, or shared advert on social media. These tools have amazing bangs, whizzes, nerd knobs, and colorful eye-popping executive dashboards which promise to deliver the “ultimate in information security” or “the final solution to solve your [insert INFOSEC pain point here]”. Sometimes they come with a cool price tag of $170,000+ (personal experience).
But when I start asking the simple questions like “What have you done up to this point to solve for [x]?” the response trends in the same direction: “Well we asked our security vendor to recommend a product…”
Timeout. What have you or your team actually implemented prior to asking your security vendor for another solution?
Rarely I get the full architectural brain dump on what has worked, what isn’t working, and the steps taken to fix, or try to fix, the problem. Those folks are looking to improve their security posture and are wisely determining how to best spend their funding. This food-for-though post is not for those folks. Most of the time, however, I get the blank stare.
Don’t skip the basics folks. It doesn’t matter if you are a small startup or a fortune 500 company. At the core of our business we all rely on the same, or a closely related, technology stack.
We can all benefit from implementing the basics (for email this means free SPF, DKIM, and DMARC) as well as user education (a topic I will discuss later). Do your part in protecting the internet from the internet bad guys and save your hard-earned INFOSEC budget for a tool set that really matters.
P.S. – Remember that email forensic analysis that I mentioned at the beginning of this post? I’m hunting down a server that is attempting to send email on behalf of my wife’s domain.