“We don’t need to buy another security tool. What we need is common sense security and somebody with the authority to fix stuff.” – John Ball
A multi-part series by John Ball, Phillip Kuzma, and Ted Nass on web server security.
 (John): I’m a fan (maybe a sucker?) for good grades. I think this is why I like SSL Labs so much. They simply grade your security, color code it, and tell you what works and what doesn’t work.
(John): I’m a fan (maybe a sucker?) for good grades. I think this is why I like SSL Labs so much. They simply grade your security, color code it, and tell you what works and what doesn’t work.
When I first ran johndball.com through SSL Labs I wasn’t using Cloudflare. I was graded with a “C” and had a lot of items that needed fixing. I fixed the issues identified on my Apache2 instance and was graded with an “A+”. Now that I’m behind Cloudflare, I can utilize some of their advanced features such as Certificate Authority Authorization. Although it doesn’t get my grade any higher it does give me some more “green” on the status page. Apparently I like green too. Matter of fact, I like Qualys’ SSL Labs so much that I proudly link to my site’s results in the web page footer.
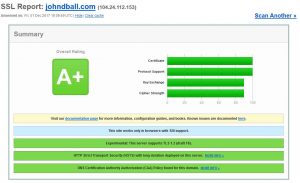 What exactly are we looking for when using their service? Well the obvious is that a better grade means better web server communication security (so to speak). What you really want to focus on is the protocols your server offers (SSL 2, SSL 3, TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3, etc.) and the cipher suites used. If you support RC4 and serve up sites negotiated with SSL 3 you have a problem. If you have weak protocols or less than desirable protocols (SSL 2, SSL3, TLS 1.0) start by turning those off. Your customers, visitors, and auditors will thank you. Re-run your server through SSL Labs to validate your results.
What exactly are we looking for when using their service? Well the obvious is that a better grade means better web server communication security (so to speak). What you really want to focus on is the protocols your server offers (SSL 2, SSL 3, TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3, etc.) and the cipher suites used. If you support RC4 and serve up sites negotiated with SSL 3 you have a problem. If you have weak protocols or less than desirable protocols (SSL 2, SSL3, TLS 1.0) start by turning those off. Your customers, visitors, and auditors will thank you. Re-run your server through SSL Labs to validate your results.
Next knock out weak ciphers. For IIS you can use the IIS Crypto Tool from Nartac Software. In Apache2 it’s a matter of navigating to your /etc/apache2/mods-enabled/ssl.conf file and making changes. Back when I started this I used Raymii.org’s blog post for direction and guidance.
Once your protocols and ciphers are locked down start moving on to the other items. Note: we began using Cloudflare universal certificates to address some items around certificate security.
Other items for addressing are:
- Certificate Transparency
- DNS CAA – Certificate Authority Authorization by Cloudflare is currently in Beta as of this posting. It was very easy to set up. We simply opened up a ticket with Cloudflare using this link and requested CAA access for our domains. CAA is cool because it requires certificate authorities to check whether or not they are listed on the domain’s DNS before issuing a certificate. This is important because it is supposed to prevent malicious persons from requesting certificates representing your domain. REF: https://blog.qualys.com/ssllabs/2017/03/13/caa-mandated-by-cabrowser-forum
- Using trusted certificates
- Secure renegotiation
- Downgrade attack prevention
- Forward secrecy
- OCSP stapling
- HSTS
- HSTS Preloading
- Public key pinning
Make a backup copy of your config and validate your results after each change. The last thing you want is a broken connection 12 changes deep.
Resources used in this post: