Since moving to a remote-work state due to COVID-19, my Microsoft Teams video quality has been “okay”. I’ve written off most of my video quality issues as a result of millions of people moving to a remote-work state.
Today I decided to take a deeper dive into my connectivity issues and it centers on my Untangle firewall, specifically the SSL inspection (MITM) app.
If you are familiar with Microsoft’s cloud technologies then this URL should be of no surprise: https://docs.microsoft.com/en-us/office365/enterprise/urls-and-ip-address-ranges#skype-for-business-online-and-microsoft-teams. The specific URL is for Skype and Teams but the entire page contains the URLs and IP ranges needed for proper access to the Office 365 infrastructure.
I had previously bypassed inspection for specific ports related to Microsoft Teams but today I went ahead and bypassed all Microsoft IPs needed to access their Skype and Teams infrastructure. Why? My SSL inspector was knocking down direct-IP connections to the Teams servers and I observed this behavior when using the “Microsoft Skype for Business Network Assessment Tool” (URL here: https://www.microsoft.com/en-us/download/details.aspx?id=53885).
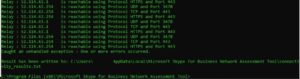
In this image, you can see the SSL inspector logs abandoning the connection to the MS IPs.
 And this was occurring while running the MS BNAT tool.
And this was occurring while running the MS BNAT tool.
After bypassing the CIDR ranges for Teams, the traffic was no longer showing up in my inspector app. I have quite a few video conferences this week which I’ll use to determine how well this implemented change holds up. I’ll update this post with my findings.
Update: this seems to have done the trick. No more dropped or delayed calls.