I’m working with a client to clean their email, SSL, and pretty much everything .php in their hosting account with InMotionHosting.com. Seems like something on the client side was hit with a PHP exploit. I found exploited files and directories by taking a full backup of the client’s hosted content and scanned with ESET Endpoint Security. Using the virus detection logs I narrowed down the client’s infected directories.
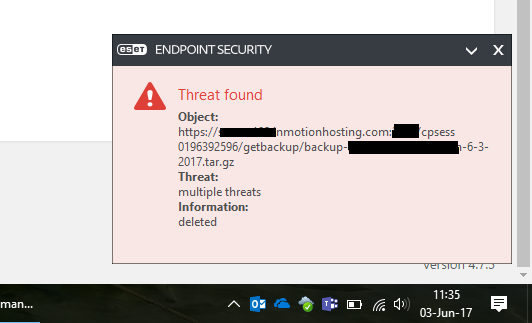
Trying to remediate manually would take forever and a day. Fortunately the client is running WordPress. This is my unorthodox method to scanning folders outside the public_html folder using the “Anti-Malware from GOTMLS.NET” WordPress Plugin.
- Log in to client’s CPanel and go to File Manager
- In File Manager, note the directories that contain infected PHP content
- In CPanel, create a CRONJOB that SYMLINKS to the infected directories
- For Anti-Malware from GOTMLS.NET Plugin, it can scan all public_html, wp-content, and wp-plugin directories. In an effort to keep things simple, I put SYMLINK files in the wp-plugin directories and executed a scan in wp-plugins.
- EXAMPLE:
ln -s /home/CLIENT/mail /home/CLIENT/public_html/wp-content/plugins/symlinkmail
ln -s /home/CLIENT/etc /home/CLIENT/public_html/wp-content/plugins/symlinketc
ln -s /home/CLIENT/logs /home/CLIENT/public_html/wp-content/plugins/symlinklogs
ln -s /home/CLIENT/ssl /home/CLIENT/public_html/wp-content/plugins/symlinklssl - Set your CRONJOB to execute in 1 minute and delete the job when finished.
- Go to the Anti-Malware from GOTMLS.NET Plugin and start a scan
- Once the GOTMLS scan is complete, remove the infections.
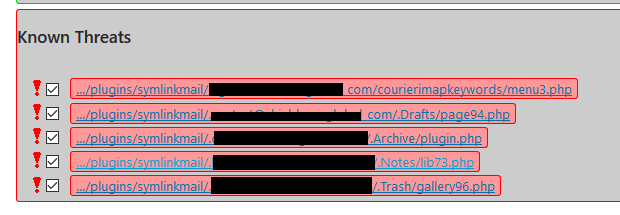
Caveats
- DO NOT attempt to remove the SYMLINKS using the CPanel file manager. Either SSH and remove the SYMLINK or call InMotionHosting support to remove the SYMLINK. If you “just delete the symlink” you’ll end up deleting content it references.
- DO NOT attempt to SYMLINK to the root directory. You will cause a SYMLINK loopback and the plugin will crash.