“If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.” – Bruce Schneier
A multi-part series by John Ball, Phillip Kuzma, and Ted Nass on web server security.
![]() Wikipedia: “HTTP Strict Transport Security (HSTS) is a web security policy mechanism which helps to protect websites against protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should only interact with it using secure HTTPS connections,[1] and never via the insecure HTTP protocol. HSTS is an IETF standards track protocol and is specified in RFC 6797.”
Wikipedia: “HTTP Strict Transport Security (HSTS) is a web security policy mechanism which helps to protect websites against protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should only interact with it using secure HTTPS connections,[1] and never via the insecure HTTP protocol. HSTS is an IETF standards track protocol and is specified in RFC 6797.”
An explanation of the benefit from Qualys: “HTTP Strict Transport Security (HSTS) is an SSL safety net: technology designed to ensure that security remains intact even in the case of configuration problems and implementation errors. To activate HSTS protection, you set a single response header in your websites. After that, browsers that support HSTS (at this time, Chrome and Firefox) will enforce the protection.
The goal of HSTS is simple: after activation, do not allow insecure communication with your website. It achieves this goal by automatically converting all plain-text links to secure ones. As a bonus, it will also disable click-through SSL certificate warnings.”
HSTS is so easy to implement on Apache2, once HTTPS is configured, it is crazy that more sites aren’t using it. Of the top 500 websites that are tracked by Hardenize.com, only 32% of those are utilizing HSTS and 7% are preloading HSTS. 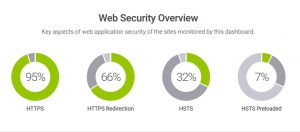 We enabled HSTS preloading in our /etc/apache2/sites-enabled/[sites].conf file. It literally is one line in your virtual host configuration:
We enabled HSTS preloading in our /etc/apache2/sites-enabled/[sites].conf file. It literally is one line in your virtual host configuration:
Header always set Strict-Transport-Security "max-age=31557600; includeSubdomains;
We tested that HSTS was deployed correctly before setting long duration by changing the “max-age” variable to “max-age=0”. You will get a warning on validation because HSTS age is set low but this confirms that it is working prior to setting a long duration on a faulty deployment.
As the definition above mentions, this ensured that insecure communication was no longer allowed with our web server. As an added layer, we also enabled HSTS on Cloudflare under the “Crypto” tab after validating our results on SSL Labs. We validated our results again in SSL Labs to ensure our changes took effect in Cloudflare then jumped over to https://hstspreload.org/ to get our domains added to the Google Chrome HSTS Preload list. This means that users of Google Chrome who have never visited our domains before would do it via HTTPS even if their browser had never visited the domain before.
We validated our results again in SSL Labs to ensure our changes took effect in Cloudflare then jumped over to https://hstspreload.org/ to get our domains added to the Google Chrome HSTS Preload list. This means that users of Google Chrome who have never visited our domains before would do it via HTTPS even if their browser had never visited the domain before.
If you’re curious about what is loaded in Firefox and Chrome there is a Stack Exchange thread on how to pull that data. https://security.stackexchange.com/questions/92954/how-can-i-see-which-sites-have-set-the-hsts-flag-in-my-browser
Resources used in this post: