Being on the law enforcement court-ordered side of the house for suspect device records and also physically processing iPhones through Cellebrite’s UFED, I wanted to see what the difference was between user-requested data and court-ordered or forensically captured data.
I navigated on over to Apple’s privacy page (https://privacy.apple.com/) and requested a copy of my data. I was curious to see what Apple had stored for me… or what Apple was going to share with me at my request. 
I selected all data and followed through the prompts. Seven days later I received an email from Apple stating that my downloadable data was ready for retrieval.

I navigated back to the Data and Privacy page and downloaded each of the content categories.
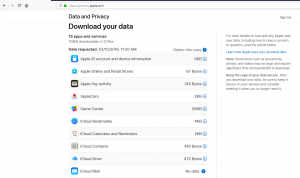
I was underwhelmed actually. There really wasn’t much there (or not much Apple was going to share). I’m not an iCloud user (I don’t sync my files to iCloud) and most of my privacy settings are set to limit exposure of personal data with Apple. Assuming Apple is sharing all they have, I’m surprised to see very little is available.
From a records request perspective, I can say that most of what I see in my account would not be provided with a valid court order. From recent experience, court ordered data requests from Apple turn up mainly meta-data of the user whereas my data request turned up content. This isn’t to say “special” government entities wouldn’t have access to the stored data. On the contrary: if Apple can provide me with content then I would assume it could be provided elsewhere using a FISA request (or other). Or just compromised and stolen.
From a forensic device processing perspective, what was in my account pales in comparison to what I can extract from a mobile device. If physical and electronic safeguards were bypassed or circumvented either through technology or force (compelled to give up a device pass code for example), then I can expect almost all available data from the mobile device including content and meta-data.
What does all this mean to the user? Well, I strongly recommend you don’t travel with sensitive personal or business information. Too many times I hear stories of foreign governments forcing users to unlock their mobile devices then taking those devices for some amount of time away to a “back room” at border control. It is simply too darn risky to be traveling with sensitive information.
It is also too risky to be conducting your entire life on a mobile device then traveling around with that device. Suppose you don’t travel across borders or aren’t worried about government interactions with your sensitive data. What happens if you lose or have your device stolen? Sometimes that could wreck your life more than a government entity could.
I think we’ve blurred the lines and forgot what telephones were originally intended for.

Remote wipe and use owncloud. Use AOSP and fon’t fork over data to companies….